Select a post to read
Home
Exploiting POST-based XSSI
We know, more and more client-side attacks are dying. But sometimes, with introduction of new features, an unexploitable becomes exploitable. Yes, combined with the power of Service Worker, XSSI is no longer limited to GET requests.
This essentially means we can also include resources with POST requests and CORS-safelisted headers. The idea is simple- intercept the request and modify to send no-cors POST request. For demonstration purpose, I’ve built a rough POC at https://cm2.
XSS with length restriction
There are situations where you can execute JavaScript but you’re limited to alert because it only allows limited number of characters. I recently saw a report on HackerOne with exact same situation- which is why I’m writing this post. The reporter managed to execute arbitrary JavaScript but made it somewhat complicated and required few user interactions. This drastically lessens the severity and no doubt, results in small reward.
The more promising Proof of Concept in case of XSS, in my opinion, is to load external JavaScript from a domain under your control.
On-site Request Forgery
You might have heard of Server Side Request Forgery or SSRF, and probably already came across On-site request Forgery. Let’s call it OSRF for brevity and not to confuse with CSRF. This post aims to briefly explain what OSRF is and how it differs from SSRF, possible impacts and remedy.
To begin with,
SSRF is a type of vulnerability where an attacker is able to influence Servers to send crafted requests to their destined location.
Forging Content-Type Header With Flash
You might already know how you can forge HTTP request headers using flash. So, to keep it short, I’m talking about Content-Type only.
Lately, I’ve been seeing tweets & reports about CSRF attack involving JSON data. In fact, I saw a tweet asking if it was safe to rely on Content-Type: application/json for CSRF protection. And, going through the replies, I found it was concluded safe- because browsers don’t yet support application/json in HTML form submission.
HackerOne XSSI – Stealing Multi Line Strings
I assume you already know what XSSI is. If not, here’s a brief introduction cited from Identifier based XSSI attacks
Cross Site Script Inclusion (XSSI) is an attack technique (or a vulnerability) that enables attackers to steal data of certain types across origin boundaries, by including target data using SCRIPT tag in an attackerss Web page as below
<!-- attacker's page loads external data with SCRIPT tag --> <SCRIPT src="http://target.
MS Edge – HTTP Access Control (CORS) Bypass
This is a short post about a vulnerability I had found in Microsoft Edge. TL;DR
Edge failed to recognize HTTP Authentication information (i.e. Authorization Header) as credential information when sending fetch requests. So, if an application uses Basic or NTLM auth, Edge would send Authorization header in all fetch requests despite specifying not to include credentials.
If you noticed, I explicitly specified not to include credentials. Yet, it was sent despite me specifying not to and you can see the response in console.
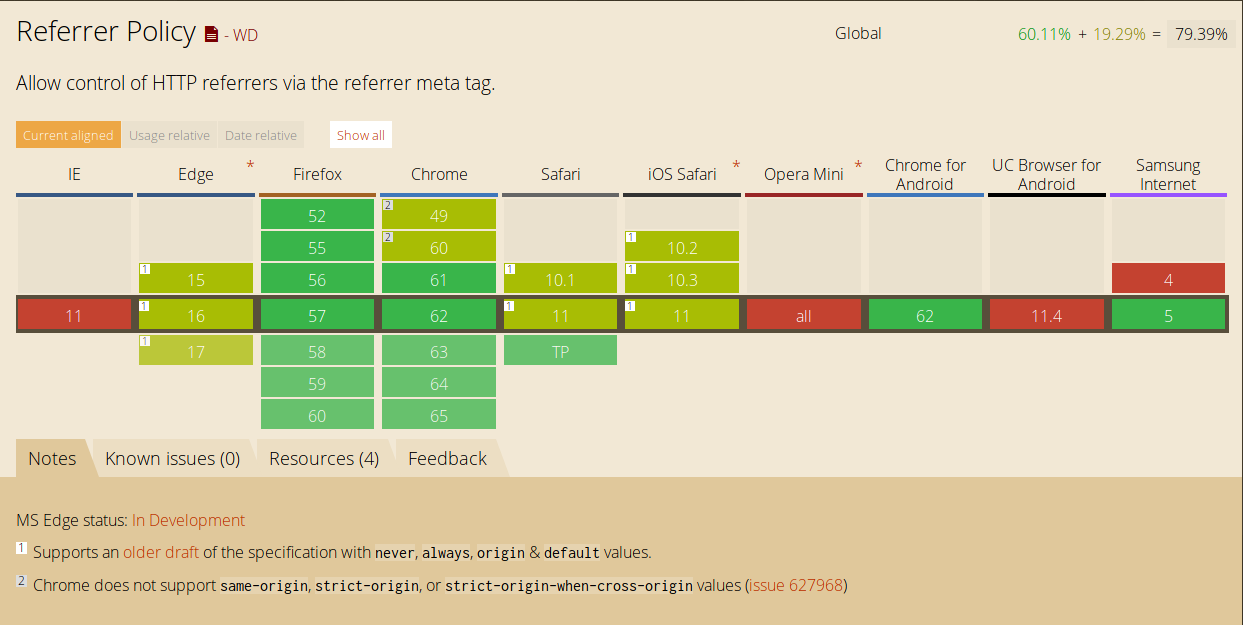
Referrer Policy
There are, atm, 5 different ways referrer policy can be delivered as defined by W3C. Setting referrer policy via meta is supported by all modern browsers (as shown above). The other ones, however, are new and aren’t widely supported or used.
The HTML Standard defines the concept of referrerpolicy attributes which applies to several of its elements, for example:
<a href="http://example.com" referrerpolicy="origin"> In general, the order in which these signals are processed are
Stealing CSVs Cross-domain
Back in 2008, Chris Evans found it was possible to steal data cross-domain in Firefox using script includes. We can still read his report at http://scary.beasts.org/security/CESA-2008-011.html
In his own words:
The modern web model permits remote domain <script> inclusion with no restrictions. If the remote data, which does not have to be script, has an effect on the evil domain doing the inclusion, you have a cross-domain data leak.